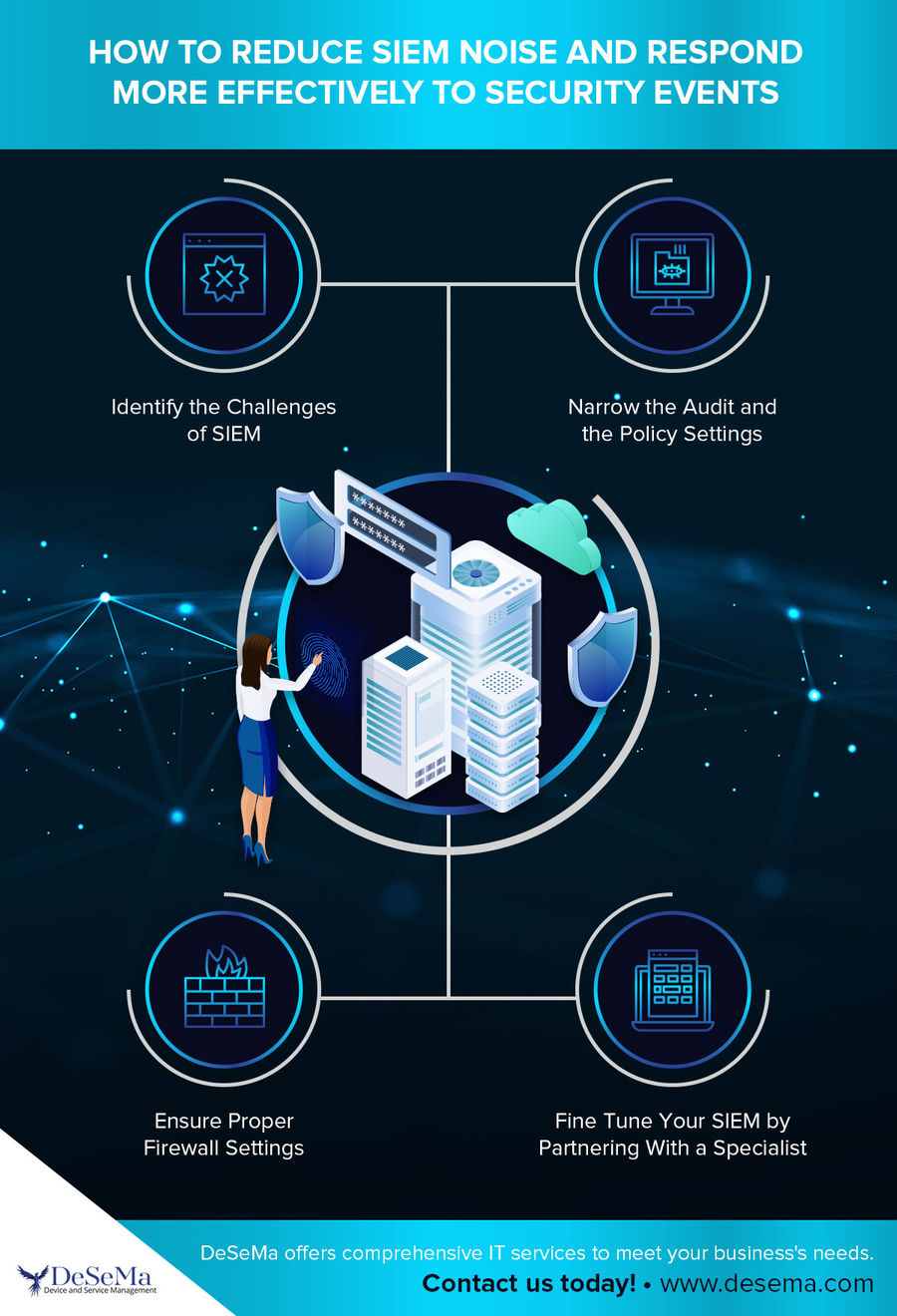
In principle, security information and event management (SIEM) sound like the solution to the challenge of detecting cyber threats. SIEM collects log files and other security data from across the enterprise and stores it in a central database. The system then correlates and analyzes the data to identify abnormal patterns that could suggest a vulnerability, threat, or active incident.
SIEM unifies data from disparate systems and single-purpose security solutions that can only recognize and understand certain data types. All security data can be analyzed and cross-referenced from a single interface, enabling human IT analysts to make better decisions. Alerts and reports are generated automatically so that the IT team can respond quickly to anomalous conditions.